The Power Corridor has not independently verified the claims, but metadata links a Chinese SIM card and a Pakistani IP address to coordinated intimidation against journalists in Manipur.
BY PC Bureau
October 30, 2025: In a stunning revelation, forensic digital evidence has linked Manipur terrorist outfits to China and Pakistan. A post on X by @JShakurB has uncovered that death threats issued to media outlets in Manipur originated from a SIM card registered in mainland China (+86 130 9948 0898), while a fake press release condemning Indian military actions was uploaded from an IP address (39.49.215.163) in the heart of Islamabad, Pakistan.
The Power Corridor has not independently verified these claims. However, the specific allegations circulating online warrant thorough investigation — and if proven true, they raise serious questions about potential external influence and the need for decisive action against those involved.
These findings expose the Vally-based terror ecosystem as a franchised arm of Beijing’s strategic leverage and Islamabad’s vendetta against India. The breakthrough came amid escalating attempts to gag independent reporting on rampant extortion rackets run by armed groups in the Imphal Valley and their imposition of a media blackout on coverage of protests led by the Manipur People’s Party (MPP).
The Chinese SIM: Direct Line for Death Threats
On an undisclosed date in late October 2025, an investigative media outlet in Manipur received a series of chilling threats via WhatsApp voice calls and messages from the number +86 130 9948 0898. The caller, identifying as a representative of Meitei terrorist groups PREPAK, demanded the immediate removal of a video exposing extortion demands and protest coverage.
“Remove the video you published immediately. And you are barred from publishing any news until May 30, 2026. Should you fail to comply with this warning, all repercussions will solely be your responsibility,” read one message, accompanied by a 3-minute voice call log.
Geolocation and telecom metadata confirmed the SIM card’s registration in China, with the country code +86 explicitly tied to mainland operators. A screenshot from a verified country code database (Filo platform) reaffirms: “The country code +86 is for China… When you see a phone number starting with +86, it means the number is registered in China.”
#breakingnews
🚨BEIJING CALLING:
Meitei Terrorists used SIM cards registered and traced to mainland China, (+86 13099480898) to silence Indian Journalists.📍Every call, every communiqué, every threats from Meitei Terrorists has reaffirms one truth: the Meitei terror ecosystem… https://t.co/87xFfaW3gz pic.twitter.com/calpa4EFzV
— J Shakur (@JShakurB) October 30, 2025
The threats were not isolated. Multiple missed calls and follow-up messages in a mix of English and local dialects (including references to “Thagatliba vdo adu yamna thuna louthou” – warning against uploading videos until April 30, with extensions to May 6) underscored a coordinated intimidation campaign. WhatsApp chat logs show the perpetrator urging compliance to avoid “fattagi daita nasana pujagadabani” (severe consequences).
This incident aligns with broader patterns: Terror groups have systematically targeted journalists covering MPP-led demonstrations against “taxation” imposed by outfits like the People’s Liberation Army (PLA) of Manipur and Arambai Tenggol. The use of a Chinese-registered SIM bypasses Indian telecom tracing, enabling anonymous cyber intimidation – a hallmark of Beijing’s hybrid warfare toolkit in border regions.
READ: Kuki Outfit Kowtows Before Muivah, Architect of 1990s Bloodshed
READ: Rio Counts the Dead After Brazil’s War on Drugs Lines Streets With Corpses
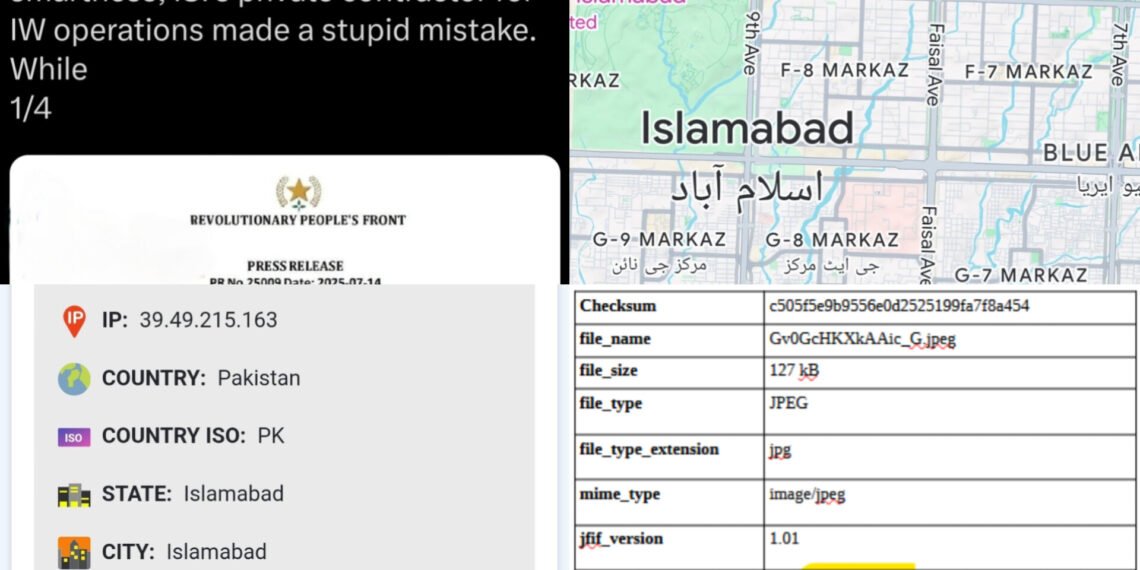
The Pakistani IP: Fake Press Release from Islamabad’s CoreIn a parallel exposure, a press release purportedly from the “Revolutionary People’s Front” – a banned Meitei outfit under the Unlawful Activities (Prevention) Act (UAPA) – condemned a recent Indian Army precision strike on a shared ULFA-PLA hideout inside Myanmar. The communiqué urged Northeast Indians to “reject Indian identity,” branded India an “occupier,” and called for anti-India slogans, including symbolic burning of the Indian flag.
Forensic analysis by @NepCorres (Nepal Correspondent) traced the document’s upload to IP address 39.49.215.163. Metadata from the JPEG file (Gv0GdHKXkAAic_G.jpeg, 127 KB) revealed:
- Device: Desktop-TVB112H
- System Model: Vmware (virtual machine, often used for anonymity)
- IPv4: 39.49.215.163
- Geolocation: Latitude 33.7215, Longitude 73.0433 – pinpointing Bahria Executive, Islamabad, along Ismail Zabeeh Road, Faisal Avenue.
- Organization: Pakistan Telecommunication Company Limited (PTCL) – a state-owned entity repeatedly implicated in Inter-Services Intelligence (ISI) operations, including espionage and honey-trapping Indian military personnel.
The file’s EXIF data, including checksum c505f5e9b9556e0d2525199fa7f8a454, confirmed upload from a VMware virtual environment, masking the true origin but failing to scrub the IP. PTCL servers in Islamabad’s F-8 and G-9 Markaz sectors (near Shah Faisal Masjid) further corroborate the location.
“This is another attempt to show over smartness. ISI’s private contractor for IW operations made a stupid mistake while [uploading] this fake press release,” noted @NepCorres in their X post, highlighting the unmasked server logs.
These twin traces – a Beijing-registered SIM for real-time threats and an Islamabad IP for propaganda dissemination – form an irrefutable arc of foreign orchestration.
Experts describe this as a “hybrid threat campaign”: Chinese cyber elements for coercion, Pakistani intelligence for ideological scripting. The Manipur conflict – pitting Meiteis against Kukis – has been hijacked, transforming ethnic grievances into geopolitical leverage